Note
This plugin is part of the community.general collection (version 2.5.1).

Sudo ufw allow 8080/tcp Opening Port Ranges # With UFW, you can also allow access to port ranges. When opening a range, you must specify the port protocol. For example, to allow ports from 7100 to 7200 on both tcp and udp, run the following command: sudo ufw allow 7100:7200/tcpsudo ufw allow 7100:7200/udp Allowing Specific IP Addresses #. # Allow everything and enable UFW-ufw: state: enabled policy: allow # Set logging-ufw: logging: on # Sometimes it is desirable to let the sender know when traffic is # being denied, rather than simply ignoring it. In these cases, use # reject instead of deny. In addition, log rejected connections:-ufw: rule: reject port: auth log: yes # ufw supports connection rate limiting, which is useful. Aug 20, 2020 sudo ufw allow PORT. As an example, let us allow access through the default OpenSSH port (Port 22). Sudo ufw allow 22 Specifying the Protocol for the Port to be Allowed On. Using this simplified syntax, you can specify the protocol that you want the port to access. By specifying the protocol, you will not be able to access it using any other. 1.关闭ubuntu的防火墙 ufw disable 2.卸载了iptables apt-get remove iptables. 1.用iptables -F这个命令来关闭防火墙,但是使用这个命令前,千万记得用iptables -L查看一下你的系统中所有链的默认target,iptables -F这个命令只是清除所有规则,只不会真正关闭iptables.想象一下,如果你的链默认target是DROP,本来你有规则来允许一些.
To install it use: ansible-galaxycollectioninstallcommunity.general.
To use it in a playbook, specify: community.general.ufw.
Set Up Default Policies. UFW is installed on Ubuntu by default. If it has been uninstalled for some.
Ufw Allow Openssh Online
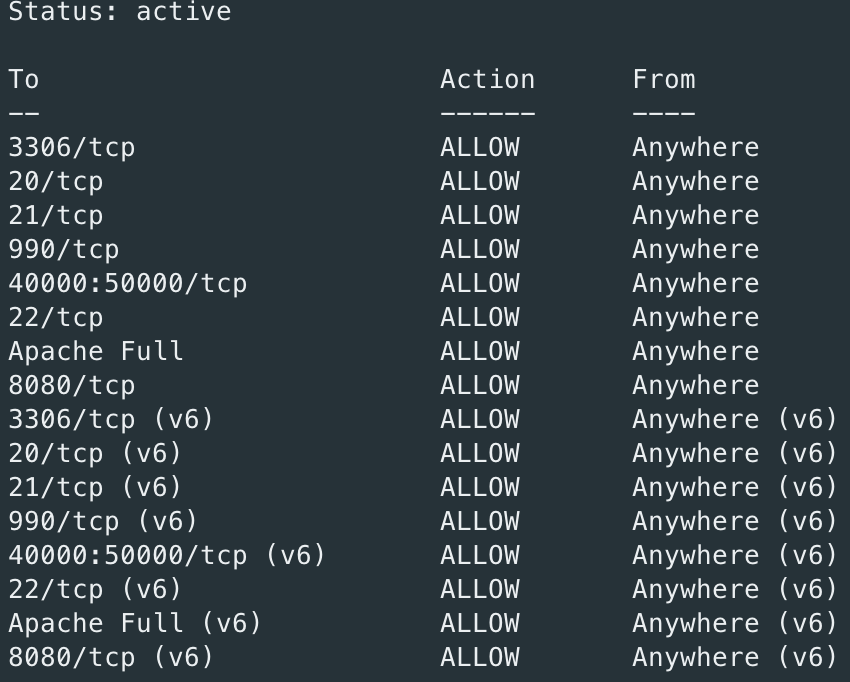
Manage firewall with UFW.
The below requirements are needed on the host that executes this module.
Sudo Ufw Allow Openssh
ufwpackage
| Parameter | Choices/Defaults | Comments |
|---|---|---|
| comment string | Add a comment to the rule. Requires UFW version >=0.35. | |
| default string |
| Change the default policy for incoming or outgoing traffic. |
| delete |
| |
| direction |
| Select direction for a rule or default policy command. Mutually exclusive with interface_in and interface_out. |
| from_ip string | Default: | Source IP address. |
| from_port | Source port. | |
| insert integer | Note that ufw numbers rules starting with 1. | |
| insert_relative_to string |
| Allows to interpret the index in insert relative to a position. zero interprets the rule number as an absolute index (i.e. 1 is the first rule).first-ipv4 interprets the rule number relative to the index of the first IPv4 rule, or relative to the position where the first IPv4 rule would be if there is currently none.last-ipv4 interprets the rule number relative to the index of the last IPv4 rule, or relative to the position where the last IPv4 rule would be if there is currently none.first-ipv6 interprets the rule number relative to the index of the first IPv6 rule, or relative to the position where the first IPv6 rule would be if there is currently none.last-ipv6 interprets the rule number relative to the index of the last IPv6 rule, or relative to the position where the last IPv6 rule would be if there is currently none. |
| interface string | Specify interface for the rule. The direction (in or out) used for the interface depends on the value of direction. See interface_in and interface_out for routed rules that needs to supply both an input and output interface. Mutually exclusive with interface_in and interface_out. | |
| interface_in added in 0.2.0 of community.general | Specify input interface for the rule. This is mutually exclusive with direction and interface. However, it is compatible with interface_out for routed rules. | |
| interface_out added in 0.2.0 of community.general | Specify output interface for the rule. This is mutually exclusive with direction and interface. However, it is compatible with interface_in for routed rules. | |
| log |
| |
| logging |
| Toggles logging. Logged packets use the LOG_KERN syslog facility. |
| name string | aliases: app | |
| proto string |
| aliases: protocol |
| route boolean |
| Apply the rule to routed/forwarded packets. |
| rule string |
| |
| state |
| enabled reloads firewall and enables firewall on boot.disabled unloads firewall and disables firewall on boot.reset disables and resets firewall to installation defaults. |
| to_ip string | Default: | Destination IP address. |
| to_port | Destination port. |
Authors¶
Ufw Allow Openssh File

Ufw Ubuntu
Aleksey Ovcharenko (@ovcharenko)
Jarno Keskikangas (@pyykkis)
Ahti Kitsik (@ahtik)
